Tor 0.2.2.34 Released with fixes of anonymity vulnerability
0
comments
vic
-
Tor 0.2.2.34 fixes a critical anonymity vulnerability where an attacker can de-anonymize Tor users. Everybody should upgrade. Clients should upgrade so they are no longer recognizable by the TLS certs they present. Relays should upgrade so they no longer allow a remote attacker to probe them to test whether unpatched clients are currently connected to them.This release also fixes several vulnerabilities that allow an attacker to enumerate bridge relays. Some bridge enumeration attacks still remain.
Download Here
Plz, Post a Thanks To Keep This Post Alive!
How to bypass/hack a Firewall
Firewall is a basic and main component for securing a network . The basic purpose of a firewall is to isolate one network from another network so that networks can't make effect on each other.Hackers often bypass Antiviruses and Anti-spywares by some methods Like Crypting,Hexing, File-pumping etc,but it becomes very difficult for a Hacker to bypass a Firewall that's why I am writing this article about How to bypass a Firewall easily.
 Now we will see How to Hack or Bypass firewall using SSH Tunneling
Now we will see How to Hack or Bypass firewall using SSH Tunneling
Firewall is often called Hindrance(Obstacle) by hackers. In the below chart ,the complete working of firewall is shown :
The method which is mostly used by Hackers to bypass firewall is known as SSH tunneling.
What is SSH Tunneling?
- Well according to wikipedia:
A Secure Shell (SSH) tunnel consists of an encrypted tunnel created through an SSH protocol connection. Users may set up SSH tunnels to tunnel unencrypted traffic over a network through an encrypted channel.
For more information on SSH Tunneling See it on Wikipedia Here
Reason to Bypass firewall
Firewall is always a problem for Hackers.Particularly if you are in university or working somewhere,you have examined that the network administrators deny access to file sharing, instant messaging or social networks such as facebook or myspace with a firewall or proxy server.So when ever you want to connect to them a message comes that these services are unavailable or something like that.To avoid this ,we have to break firewall so that we may access these services.SSH Tunneling
 Now we will see How to Hack or Bypass firewall using SSH Tunneling
Now we will see How to Hack or Bypass firewall using SSH Tunneling- First of all Create an account for SSH access.There are many sites which provide paid and free SSH access.One of them is Superprotocol .
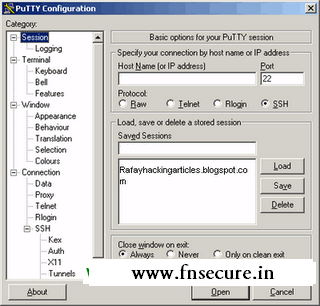
- Now download an open source SSH Client named Putty .
- After downloading ,execute the software and run it.
- Now you will come to this configuration settings page.
- Now in the host name,enter the server through which we can connect SSH access.make sure SSH is selected using port 22.
- Next, in the SSH options,click on Tunnels,here we will set up a Tunnel.
- Change the Source port to 8080 and then click on Dynamic.
- After doing all this click on Open.
- Now login in with username and password which we given in SSH Provider.
- Establishing the tunnel part is completed now.
Wire Shark Instalation
- Now we need to Download another software named Wire Shark and execute wireshark.
- Now start Packet capture,in the beginning it will be empty.
- Open google.com in your browser and then packets getting captured by the software.
Configuring Mozilla
Now the next part is the configuring of Mozilla Firefox so that we can use SSH connection.- Open the Mozilla browser and open "Tools" menu and then "Options".
- Click on "Advanced" button tab, and then "Network" tab, and then click on "Settings".
- Now you are in Connection Settings enter "localhost" as the "Socks Host and port number, such as "1080" into the "Port:" field.
- Now come back to wire shark you will see some SSH connection but now there's no information about what is being sent from server to client.
How to use proxy easily in Backtrack 5
Hey guys how u been ??? hope u enjoying , huh !!!
There are a lot of ways to hide your identity , either by single proxy or by multiple proxies like TOR which Xeo Hacker explained in a recent post.
But if u have BackTrack then nothing to worry about you can use proxy very easily and u can use multilple proxies also.
Well its called proxychains ..
So lets get started
Well proxychains is a inbuilt tool in backtrack to let u use proxy very easily. It uses proxy according to the configuration file , which we gonna config and it takes u to any address or url via multiple proxies.
well actually there is a configuration (.conf) file in etc folder . its named proxychains.conf . This is the file where u will do all ur stuffs and u'll hide your identity just by typing a single command once you configure.
Go to terminal and type following command then hit enter
Wat happened ??? there is a gedit window opened with some text in it ... its actually ur config file
There are 3 modes of proxychains
There are a lot of ways to hide your identity , either by single proxy or by multiple proxies like TOR which Xeo Hacker explained in a recent post.
But if u have BackTrack then nothing to worry about you can use proxy very easily and u can use multilple proxies also.
Well its called proxychains ..
So lets get started
wat it does
Well proxychains is a inbuilt tool in backtrack to let u use proxy very easily. It uses proxy according to the configuration file , which we gonna config and it takes u to any address or url via multiple proxies.
proxychains intro
well actually there is a configuration (.conf) file in etc folder . its named proxychains.conf . This is the file where u will do all ur stuffs and u'll hide your identity just by typing a single command once you configure.
Go to terminal and type following command then hit enter
gedit /etc/proxychains.conf
Wat happened ??? there is a gedit window opened with some text in it ... its actually ur config file
Modes or types of proxychains
There are 3 modes of proxychains
- dynamic_chain:This uses the list of proxies in the same order as u placed
- strict_chain:almost similar to previous one except it will not work if it gets any dead proxy server
- random_chain:this is the best .. this chooses and uses proxies randomly
Configuration of the file
u have to open that file with root privilege to edit that file so first issue following command
sudo suthen issue this command
gedit /etc/proxychains.confnow you have to follow these steps
- comment out the mode u want to use

as u can see i have commented out random_chain by "//" .
- now go to any proxy server list .. just google it .. i'll be using socks4 proxy servers so search on google .. then copy some IPs and their port no. and then paste it where it says add proxy here . refer the pic at last i have added some IPs.
Now your configuration is done .....
How to use proxychains
to use proxychains just have to issue some commands as listed below.
proxyresolv [the site u want to open]
proxychains firefox [the site u want to open ] (for firefox)
Preview YouTube ‘Like Bar’ On Video Thumbnail
What is YouTube Rating Preview
YouTube Ratings Preview is a Chrome extension and by using this extension we can see the like bar on the thumbnail of a video in both search results and suggested videos,and we can easily judge that whether the video is worth watching or not.
Note : This extension works only for Chrome.
Most advanced and dangerous malware for Apple products - Why you should be concerned !
Indian security researcher from MalCon has created an advanced and dangerous malware for Apple products which can not only compromize your privacy but also steal important data and let hackers control your device by simple text messages.
If you are using any Apple product such as iPhone, iPad or iPod, then you shuuld be concerned. Indian security researcher from MalCon, Atul Alex has created an advanced malware for the Apple products which can not only intercept calls of users, steal data, but also provide a reverse VNC to see remotely all the actions of the victim.
However, over 90% of users normally jailbreak their devices. iOS jailbreaking, or simply jailbreaking, is the process of removing the limitations imposed by Apple on devices running the iOS operating system through use of custom kernels. Such devices include the iPhone, iPod Touch, iPad, and 2nd Gen Apple TV. Jailbreaking allows users to gain root access to the operating system, allowing iOS users to download additional applications, extensions, and themes that are unavailable through the official Apple App Store. A jailbroken iPhone, iPod Touch, or iPad running iOS can still use the App Store, iTunes, and other normal functions, such as making telephone calls.
The malware malware boasts of the following features:
• Control devices by SMS
• Invisible Malware
• VNC Server to view remote screen
• Record and listen to all calls remotely
• Upload / Download user Data
• Access all mails and texts
The Malware will be demonstrated next month at the upcoming International Malware Conference, MalConin Mumbai, India. The researcher Atul Alex has previously coded and demonstated a custom malicious firmware for Symbian last year.
Anonymous DDOS Oakland police site after violence
Cyber activists associated with Anonymous have targeted the Oakland Police Department (OPD) and other law enforcement agencies that participated in a controversial crackdown against OccupyOakland protestors. A DDOS (distributed denial-of-service) attack against the department's websitewww.oaklandpolice.com is underway, and the website currently is unreachable.
AnonyOps tweet "I'm amazed and proud of #occupyOakland protesters who stood defiant, peaceful in the face of lethal force by Oakland PD."
AnonyOps tweet "I'm amazed and proud of #occupyOakland protesters who stood defiant, peaceful in the face of lethal force by Oakland PD."
Police fired a number of tear gas canisters, concussion grenades, rubber bullets and non-lethal rounds at demonstrators on Tuesday night, drawing widespread condemnation for the use of heavy-handed tactics against unarmed civilians.
The attack was first announced via Anonymous' AnonOps Twitter feed. "@Anon_Central: Admin/User/Password Dump of oaklandnet.com Problem Oakland authorities? F--- you! >>pastebin.com/S8VRwRxQ #Anonymous," read AnonOps' tweet.
Reports of police violence against Oakland protesters re-emerged Tuesday on the movement's Web site,occupyoakland.org. The Web site published statements charging the U.S. police of numerous acts of brutality, during a recent raid designed to evict protesters from their encampment.
The most seriously injured victim was Scott Olsen, an Iraq War veteran, who suffered a fractured skull after being struck by a police projectile. His condition was upgraded to "fair" today, according to reports. According to the Pastebin document, Anonymous is offering a "no questions asked" $1,000 reward for information about the officer who threw the projectile at Olsen.
How to Beat Evil Governments When Your Internet Turned Off ?
Bruce Sutherland explain at DefCon 19 Conference that "How To Get Your Message Out When Your Government Turns Off The Internet" . Bruce Sutherland is a network systems architect and software developer with Domex Computer Services Inc, based in Melbourne Beach, FL.
How would you communicate with the world if your government turned off the Internet? Sound far-fetched? It isn't. It already happened in Egypt and Lybia and the US Congress is working on laws that would allow it to do the same. In this talk we'll explore how to get short messages out of the country via Email and Twitter in the event of a national Internet outage. Remember, data wants to be free.
Bruce has worked in the industry for over 20 years and has recently been working on building and hardening web-based applications. He has been an amateur radio operator since 2003 and enjoys making contacts worldwide via amateur radio satellite and on the traditional HF bands.
Download Complete PDF presentation here.
Malware for xbox Kinect created by 15 years old Indian researchers
Indian researchers from MalCon have created a malware that utlizes Microsoft Kinect to secretly capture pictures and upload to a picasa account.
Kinect for Xbox 360, or simply Kinect, is a motion sensing input device by Microsoft for the Xbox 360 video game console. With over 10 million devices sold till date, the kinect holds the Guiness book for world record for the fastest selling consumer electronics device - and is exactly the reason why the malware is a concern.
In recent months, there have been a number of innovative kinect hacks that make use of the kinect using both Open source drivers and the Kinect SDK. The malware, code-named 'gawde' after its creators name, works on Windows 7 to secretly capture pictures of the victim / surroundings from a connected Kinect device and uploads them to a picasa account.
Rajshekhar Murthy, Director at ISAC, (Information Sharing and Anaysis Center), a scientifc non-profit body that holds the International Malware Conference, MalCon said. "We believe that in coming years, a lot of windows based applications will be developed for Kinect and the device will gain further immense popularity and acceptance- and from a perpective of an attacker, such a popular device can be an exciting target for visual and audio intelligence. At MalCon research labs, we promote proactive security research and the malware utilizing Kinect is only a proof of concept. "
The kienct malware 'gawde' goes a step ahead and even uses voice recognition to execute a program based on keyword, without the knowledge of the victim. The malware PoC will be demonstrated at the upcoming MalCon 2011 in Mumbai, India.
Sponsor
Cyber Security, News & Support, and Technology. Follow Us, Stay Connected and Be Safe.
Share It With Friends
Blog Archive
-
▼
2011
(609)
-
▼
October
(394)
- Tor 0.2.2.34 Released with fixes of anonymity vuln...
- How to bypass/hack a Firewall
- How to use proxy easily in Backtrack 5
- Preview YouTube ‘Like Bar’ On Video Thumbnail
- Most advanced and dangerous malware for Apple prod...
- Anonymous DDOS Oakland police site after violence
- How to Beat Evil Governments When Your Internet Tu...
- Malware for xbox Kinect created by 15 years old In...
- Facebook EXE attachment Vulnerability can Compromi...
- US satellites was victim by Chinese Hackers
- Top 15 Security/Hacking Tools & Utilities
- Password Cracking with Rainbowcrack and Rainbow Ta...
- 23 Stunning Examples of Underwater Photography
- Exclusive & Stunning Examples Of Conceptual Photog...
- 10 Best Photo Editing Software for Android Users
- Best Photograph by Jonathan van Smit
- Lens Test: Nikon 35mm f/1.4G ED
- 30 Stunning Photography Captured in Fog
- 40 Breathtaking Examples of Photo Manipulation
- 20 Dazzling Examples of Motorsport Photography
- 4 Most Important Wedding Photography Lenses
- Tutorial : All Adobe Photoshop CS5 Shortcuts (Part 1)
- 10 Steps to Become A Photoshop Expert
- 5 Best Photo Editing Software for Blackberry Users
- Infographic: The Social Network Decision Tree
- 'Anonymous' Promises to Hack Into TSX on 7th November
- How to Knock Down a Website Using XSS Attack
- What is xss attack .. Xss Attack Details
- Download Different Glyphs of the New Indian Rupee ...
- Importance of Main Navigation Bar for a Website/Blog
- Top 5 Ways to Monetize Your Blog
- 25 Ways to Drive Quality Traffic To Your Blog & We...
- 5 Ways to Blog While You’re Away From Your Computer
- Simple Tips or Ways to Monetize your Blog
- 5 Simple Ways To Equip Your Blog's & Websites With...
- 7 Great Ways To Promote Your New Blog
- Add Country Flag & Frames To Google Plus Profile P...
- Read Google Plus Notifications on Your Desktop
- Add Cool Image Effects To Google+ Profile Photos I...
- How to cross post from google plus to blogger or b...
- Play Angry Birds on Google Plus
- Google Plus template for Bloggers
- How to use Google Plus ? Is it a threat for facebook
- How To Delete Circles In Google Plus?
- How To Invite Friends In Google Plus & Create Circ...
- G++ Adds Facebook & Twitter Stream In Google+ With...
- Facebook Messenger Application Updated - New Featu...
- BACKTRACK : The credential harvester attack
- Play your songs in GTA vice city
- Check the Profiles of Founder of Facebook - A simp...
- What to Do, when a thief forced you to take money ...
- Metasploit 4.1 and Armitage: What's New?
- Adobe Flash Zero-day Exploit Which Allowing Others...
- Win32/EyeStye
- Malicious Software Removal Tool Skip the details a...
- How can I make my blog load faster?
- BruCON Agnitio workshop Slides and Video Demonstra...
- Phising and how to reverse phising tut ...
- IIS 4 exploit
- Canonical releases Ubuntu 11.04 Alpha 3 !
- Make Your Own Real Android Robot !
- Warner Bros. to deliver movies on Facebook !
- Google Chrome Gets Updates: New Interfaces, Faster...
- Internet Explorer and Safari first to fall at Pwn2...
- BlackBerry Hacked via Drive-By Download at Pwn2Own !
- MHTML vulnerability under active exploitation !
- EgY SpIdEr ShElL : Shell strongest in the history ...
- 26 Underground Hacking Exploit Kit available for D...
- Exploitsearch.net - Exploit & Vulnerability Search...
- WD TV Live Hub Compromised - Multiple Vulnerabilit...
- War Texting : Hackers Unlock Car Doors Via SMS
- Get Ready for Microsoft 13 updates for August Patc...
- Google buy Reverse Engineering Company Zynamics (G...
- Hackers leak Citigroup CEO’s personal data after O...
- iPhone can be used as spy phone to get desktop Key...
- iPad 2 iOS 5 Lock Screen Bypass Vulnerability
- Adobe Flash bug allow spying Webcam hole
- Stuxnet's Son "Duqu" Removal Tool released by Bitd...
- Anonymous Hackers Take Down 40 Child Porn Websites
- Cross Site Scripting(XSS) Complete Tutorial for Be...
- Introduction to Web Application Firewall (WAF) ~ W...
- Hacking website using SQL Injection -step by step ...
- Hacking Autorun.inf virus attack|Is autorun.inf vi...
- C++ ,Batch Virus code to disable All Hard disk
- What is Your Password ? How the Password should be?
- How to Prevent from the Phishing Web page using Do...
- Hacking Using Doxing -Doxing Complete Hacking Tuto...
- What is Doxing? Trace Peoples with Doxing
- Hash Code Cracker 1.2
- How to Create your own Run Command ?
- NoScript Anywhere (NSA) Firefox Security Add on Av...
- Learn Web Application Exploits and Defenses for fr...
- Google partnered with Citizens Advice Bureau provi...
- KickAssTorrents(Kat.ph) infected and serving malwa...
- Pendrive Sniffing
- How to Install Android on Virtualbox
- Switch and Create Between Profiles Easily in Firef...
- Free one year license key
- Sony's 3D Display is Coming Soon
- Add a Note above Comment Box - To Make Comment For...
-
▼
October
(394)
About Me
Tag Cloud
Admin Tools
(16)
Adobe
(1)
Adsense
(12)
Airtel Hacks
(1)
Android
(9)
Anonymous Hackers
(2)
Apple
(14)
Applications
(3)
ATM Machine
(1)
Backtrack
(3)
Batch Files
(1)
Blackberry
(1)
Blogger
(17)
Browsers
(1)
Bugs
(2)
Business
(1)
C source code
(2)
Camera Hack
(1)
Chat
(1)
Chrome Os
(1)
computer_tricks
(122)
Computing
(4)
Corporate
(9)
Cracks
(5)
Crimes
(2)
Cyber Attacks
(12)
Cyber Crimes
(4)
Cyber Security
(51)
Cyber Threat
(19)
cyber_news
(30)
Database Hacking
(8)
Defaced
(2)
Dos
(1)
Dos Commands
(1)
Dos Tricks
(2)
Downloads
(7)
E_Books
(8)
Easy Applications
(6)
Email Security
(1)
Emails
(2)
Encryption Tools
(2)
Entrepreneur
(3)
Ethical Hacking Tools
(53)
Ethical Hacking Tutorial
(134)
Ethical Hacking Videos'
(12)
examples
(5)
Exploit
(19)
Facebook
(36)
Fakes
(1)
Featured
(19)
Footprinting
(3)
Gadgets
(20)
Gadgets_news
(14)
games
(3)
Gmail
(5)
Google
(32)
Google Dorks
(2)
Google+
(17)
Hacked
(3)
Hackers
(16)
Hacking
(74)
Hacking News
(4)
Hacking Softwares
(139)
Hacking Techniques
(112)
Hacking Tools
(144)
Hacking_news
(45)
Hacking_terms
(38)
Hackng with Mobile
(4)
Internet_Tricks
(3)
Java-Script Hacks
(1)
Keyloggers
(2)
Keys
(1)
Laptops
(1)
Latest Mobile Phones
(3)
Lecture
(1)
Linux
(6)
Loophole
(10)
Making Applications
(1)
Metasploit
(1)
Mobile
(11)
Mobile Applications
(3)
Mobile_tricks
(15)
Network Security
(6)
news
(50)
Nokia
(2)
Notepad Hacks
(1)
Operating Systems
(11)
Oracle
(1)
Password Cracking
(9)
Pendrive
(3)
penetration testing
(32)
phase_hacking
(9)
phishing
(6)
Photoshop
(11)
Programs
(1)
Protection Tools
(17)
Proxy
(2)
Scripting
(1)
Secure Computing
(38)
Security Bleach
(5)
Seminars_Work Shops_Demo
(5)
SEO
(15)
shell
(2)
shortcuts
(2)
Social Networking
(6)
Software
(70)
source
(4)
source code
(4)
SQL Injection
(9)
System security
(30)
Techie
(4)
Technology
(5)
The Pirate Bay
(1)
Torrent
(1)
Touch
(5)
Ubuntu
(3)
Updates
(2)
Video Tutorials
(4)
Virus
(20)
Vulnerability scanner
(9)
Vulnerable
(11)
Web Security
(13)
Web Traffic
(1)
Wifi Cracking
(2)
Windows
(7)
Windows Xp Tricks
(4)
Wireless hacking
(7)
workshop
(2)
Workshops and Seminars
(2)
worms
(1)
Xss Attack
(2)
Yahoo Messenger
(1)





















