HP Palm Touchpad Runs WebOS Specs
0
comments
FN Downloads
-
Details
· 9.7 inch Display with 1024x768px resolution · Weight – 1.6pounds / 740 grams · 13.7 mm thickness · 240mmx190mmx13.7mm · Dual Core CPU 1.2 GHz from Qualcomm Snapdragon dual-CPU APQ80601.2GHz · 1.3 MP camera with Video calling · Stereo speakers · 6300 mAh Battery · 3.5mm audio jack · microUSB connector · Wi-Fi b/g/n Bluetooth 2.1 + EDR · Memory : 16 GB or 32GB · Audio formats: DRM-free MP3, AAC, AAC+, eAAC+, AMR, QCELP, WAV · Video formats: MPEG-4, H.263, H.264 · Gyro, Accelerometer , Compass, light sensor · Browser with Full Flash support · Features Synergy which can sync all your personal information easily · Accessories such as Keyboard dock and Touchstone |

Dell present a new world of touch "Dell Inspiron duo"
Sometimes you want to touch. Sometimes you need to type. With the new touch-sensitive. Dell present a new world of touch dell Inspiron™ duo convertible tablet.
· The method of flip design lead you from touch to type in seconds
· Listen to music, use as an alarm clock or view your photos
· Read books, watch movies and play games on high-definition display
Specifications
Processor and Memory | · Intel® Atom™ N550 (1.5GHz, 1M Cache) · 2GB DDR3, 800MHz, 1 DIMM |
Hard Drive and Multimedia Drives | · 320GB 7200RPM hard drive · Optical drive: not included |
Audio, Video and Graphics | · Integrated audio · Intel® NM10 Express |
Connectivity | · Wireless 802.11n · Bluetooth 3.0 combo card |
Ports/Slots | · 1 Microphone · 1 Headphone · 1 SIM card slot · 2 USB 2.0 · 1 AC adapter connector |
Display, Keyboard and Webcam | · 10.1" Widescreen HD (1366 x 768) Multi-Touch Display · Touch Screen: Capacitive Multi-Touch technology · Built-in 1.3MP webcam |
Power | · 4-cell Li-ion battery (29 WHr) |
Operating System | · Genuine Windows 7 ® Home Premium (32-bit) |
Additional Software and Information | · Microsoft® Office Starter 2010 · Adobe Reader 9.0 multi-language · McAfee SecurityCenter with anti-virus, anti-spyware, firewall – 30 day trial · Stage Software |
i-Phone GPS App Crowd sources Traffic Conditions

i-Phone GPS App Crowd sources Traffic Conditions:
Have you ever been running late to an important business meeting or client presentation only to find yourself stuck in a two-mile traffic jam due to an accident on the highway, or having to reroute around a flooded road? Of course you have. Checking traffic conditions ahead of time can be helpful, but it's even better if you can get real-time updates from those in the best position to know the current conditions--other drivers.
Television and radio news outlets do their best to keep drivers informed of current traffic conditions, but there are only so many "eye in the sky" traffic copters. The truth is, much of the traffic reporting information that these news outlets have comes from actual drivers on the road calling in to report conditions as it is. Why not cut out the middle-man and just share traffic news with each other?
Waze has launched a voice-based hazard reporting feature for its iPhone GPS app. Combining GPS navigation with crowdsourced real-time traffic updates can help iPhone users stay aware of adverse road conditions, avoid delays, and get to their destinations safely and on time.
Facebook to open sales office in Hong Kong..
Facebook to open sales office in Hong Kong
Facebook, the world's largest social-networking site, will open a sales office in Hong Kong, in a move to tap the region's booming Internet scene, local media reported on Wednesday.
The Hong Kong office will service brands, companies and agencies in Hong Kong and Taiwan that want to advertise or launch marketing campaigns on its website, the company said in a statement posted on Asia Media Journal's.
Grid Computing VS Cloud Computing
Most of the people think Grid Computing and Cloud computing are same, but they are totally different. Both grid and cloud computing are networks which abstract processing tasks. Abstraction masks the actual complex processes taking place within a system, and presents a user with a simplified interface with which they can interact easily. The idea is to be able to make the system more user-friendly.
What is cloud computing?
In simple Cloud computing is sharing of resources by many users, for example imagine a company which had been formed recently with physical infrastructure such as buildings and computers, they cant spend further money on software. Thus they come towards cloud where they have to pay only for the resources which they are using, it helps them to save money.
What is grid computing?
Grid in other hand is a combination of resources from different domains. They are the true Distributed Systems, a supercomputer is a good example of a Grid computation where it follows a path to get the required resources unlike the cloud. What this means is that your grid-enabled application is not tied to the computer on your desk, it can seamlessly use more than one computer and other resources even beyond the walls of your building to boost its performance.
Real Difference between Grid and Cloud?
So what’s making cloud so special when compared to Grid, the answer is simple. When an application fails in one node, the other application on the other node may also fail, thus bringing the problem of availability in Grid. A Cloud would usually use a grid. A grid is not necessarily a cloud or part of a cloud. Thus they are two different identity with nearly common goals.
Complete Overview of Xoom Tablet From Motorola
Read more
Attackers target world's busiest stock exchanges
Attackers target world's busiest stock exchanges
British and US stock exchanges enlisted security services to thwart cyber attacks.
British and US stock exchanges enlisted the help of the security services after finding out they were the victims of cyber attacks. The London Stock Exchange is investigating a terrorist cyber attack on its headquarters last year, while US officials have traced an attack on one of its exchanges to Russia.
The Times said that was told by ‘well-placed intelligence sources' that the London Stock Exchange was trying to find the source of the attack, while a cyber security expert is reported as saying that the threat is ‘advanced and persistent'.
British govt. computers under cyber Threats
British govt. computers under cyber attacks from hostile states
British Foreign Secretary William Hague has said that cyberspace is allowing criminals and hostile intelligence agencies to attack the British government.
During a conference in Munich, Hague not only talked about how government computers were infected by a virus last year, but also detailed an attempt to steal data from a UK defence contractor. He stressed that someone in disguise of an employee of another defence firm had designed to steal information, the BBC reports.
Hotmail delivers aliases to help you manage and secure your email account.
Hotmail delivers aliases to help you manage and secure your email account.
Starting today, you can create and manage multiple email aliases from a single Hotmail account. Together with features that we introduced in November that let you use Hotmail with any existing email address, the new aliasing feature makes it easy to use a different email address and still get all the benefits of Hotmail without having to change your primary email address and online identity.
The email address a person uses is a big part of their online identity. The average person maintains three different email addresses in order to organize different types of email, maintain different personas, or keep junk mail away from a primary email address. So there are many good reasons that people want multiple email addresses, but maintaining multiple accounts, with different user names and passwords that require you to check multiple inboxes, is inefficient. With today’s update, Hotmail helps you save time by making it easier to manage your current and future email addresses in one place.
Aliases
Hotmail (and many other email services) already allow you to just add a plus sign (‘+’) and a descriptive word to the first part of your email address. For instance, if your email address was doctor-smith@live.com and you wanted to create an alias for online shopping, you could use doctor-smith+shopping@live.com. Email sent to this alias will still be delivered to your inbox or to a particular folder. This can help with managing different types of incoming email. In addition to the plus feature, we’ve also released Sweep to help manage this type of incoming email traffic.
Orkut - Security Alert! Beware of the “BOM DIA” Scrap!
The scrap just said words like bomb amungu, bom Dia etc. Soon I noticed that many people have received the same! We are started investigating the issue to find that it’s a worm stealing Orkut and Google accounts cookies and automatically posting scraps. It also automatically makes you join some communities. Here’s some important things to do while Google’s team resolves this issue –
1. If you get the bom dia scrap from any of your friend, close the Orkut immediately. DO NOT visit your friend’s profile otherwise your cookies will also get stolen and your account will be used to post scrap to your friends.
Create your own Text to speech converting software
Hi frndz...Now I am going to show you how to create your own software i.e. its just an VB script which makes you Computer to speak whatever you input...!
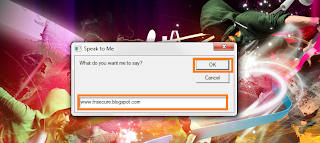
Open the file and write what you want to make your system to speak and hit OK.
This is a VB script. Just Open Notepad and copy the below script,
Dim message, sapi
message=InputBox("What do you want me to say?","Speak to Me")
Set sapi=CreateObject("sapi.spvoice")
sapi.Speak message
message=InputBox("What do you want me to say?","Speak to Me")
Set sapi=CreateObject("sapi.spvoice")
sapi.Speak message
Save the file as ANYTHING .vbs and close notepad.
Open the file and write what you want to make your system to speak and hit OK.
Dats it...
Thanks for “AYTECK” on “HF” for this awesome script...!!
Top 10 Web hacking techniques of 2010 revealed
Top 10 Web hacking techniques of 2010 revealed
A Web hack that can endanger online banking transactions is ranked the No. 1 new Web hacking technique for 2010 in a top 10 list selected by a panel of experts and open voting.
A Web hack that can endanger online banking transactions is ranked the No. 1 new Web hacking technique for 2010 in a top 10 list selected by a panel of experts and open voting.
Called the Padding Oracle Crypto Attack, the hack takes advantage of how Microsoft's Web framework ASP.NET protects AES encryption cookies.
FROM THE SECURITY WORLD: Quirky moments at Black Hat DC 2011
If encryption data in the cookie has been changed, the way ASP.NET handles it results in the application leaking some information about how to decrypt the traffic. With enough repeated changes and leaked information, the hacker can deduce which possible bytes can be eliminated from the encryption key. That reduces the number of unknown bytes to a small enough number to be guessed.
The developers of the hack -- Juliano Rizzo and Thai Duong -- have developed a tool for executing the hack.
Padding Oracle was voted No. 1 by a voting process that included Ed Skoudis, founder of InGuardians; Girogio Maone, the author of NoScript; Armorize CEO Caleb Sima; Veracode CTO Chris Wysopal; OWASP Chairman and CEO Jeff Williams; security consultant Charlie Miller of Independent Security Evaluators; IOActive director of penetration testing Dan Kaminsky; Steven Christey of Mitre; and White Hat Security vice president of operations Arian Evans.
The ranking was sponsored by Black Hat, OWASP and White Hat Security, and details of the hacks will be the subject of a presentation at the IT-Defense 2011 conference next month in Germany.
Here are the rest of the top Web hacks voted in the competition:
Evercookie -- This enables a Java script to create cookies that hide in eight different places within a browser, making it difficult to scrub them. Evercookie enables the hacker to identify the machine even if traditional cookies have been removed. (Created by Samy Kamkar.)
Hacking Autocomplete -- If the feature in certain browsers that automatically completes forms on Web sites (autocomplete) is turned on, script on a malicious Web site can force the browser to fill in personal data by tapping various data stored on the victim's computer. (Created by Jeremiah Grossman.)
Attacking HTTPS with Cache Injection -- Injection of malicious Java script libraries into a browser cache enables attackers to compromise Web sites protected by SSL. This will work until the cache is cleared. Nearly half the top 1 million Web sites use external Java script libraries. (Crated by Elie Bursztein, Baptiste Gourdin and Dan Boneh.)
Bypassing CSRF protections with ClickJacking and HTTP Parameter Pollution -- Gets around cross site request forgery defenses and tricks victims into revealing their e-mail IDs. Using these, the attackers can reset the victim's passwords and gain access to their accounts. (Created by Lavakumar Kuppan.)
Universal XSS in IE8 -- Internet Explorer 8 has cross-site scripting protections that this exploit can circumvent and allow Web pages to be rendered improperly in a potentially malicious manner.
HTTP POST DoS -- HTTP POST headers are sent to servers to let them know how much data is being sent, then the data is sent very slowly, eating up the servers' resources. When many of these are sent simultaneously, the servers are overwhelmed. (Created by Wong Onn Chee and Tom Brennan.)
JavaSnoop -- A Java agent attached to the target machine communicates with the JavaSnoop tool to test applications on the machine for security weaknesses. This could be a security tool or a hacking tool, depending on the user's mindset. (Created by Arshan Dabirsiagh.)
CSS History Hack in Firefox without JavaScript for Intranet Port Scanning -- Cascading style sheets, used to define the presentation of HTML, can be used to grab browser histories as victims visit Web sites. The history information can be used to set the victim up for phishing attacks. (Created by Robert "RSnake" Hansen.)
Java Applet DNS Rebinding -- A pair of Java applets direct a browser to a pair of attacker controlled Web sites, forcing the browser to bypass its DNS cache and so make it susceptible to an NDS rebinding attack. (Created by Stefano Di Paola.)
Sponsor
Cyber Security, News & Support, and Technology. Follow Us, Stay Connected and Be Safe.
Share It With Friends
Blog Archive
-
▼
2011
(609)
-
▼
February
(16)
- HP Palm Touchpad Runs WebOS Specs
- Dell present a new world of touch "Dell Inspiron duo"
- i-Phone GPS App Crowd sources Traffic Conditions
- Facebook to open sales office in Hong Kong..
- Grid Computing VS Cloud Computing
- Complete Overview of Xoom Tablet From Motorola
- Attackers target world's busiest stock exchanges
- British govt. computers under cyber Threats
- Hotmail delivers aliases to help you manage and se...
- Orkut - Security Alert! Beware of the “BOM DIA” Sc...
- Create your own Text to speech converting software
- Top 10 Web hacking techniques of 2010 revealed
- Microsoft warns: 900 M Internet Explorer users at...
- Facebook Founder Mark Zuckerberg's fan page has be...
- How To Identify Fake Email ID ?
- How To Remove Shortcut Virus ?
-
▼
February
(16)
About Me
Tag Cloud
Admin Tools
(16)
Adobe
(1)
Adsense
(12)
Airtel Hacks
(1)
Android
(9)
Anonymous Hackers
(2)
Apple
(14)
Applications
(3)
ATM Machine
(1)
Backtrack
(3)
Batch Files
(1)
Blackberry
(1)
Blogger
(17)
Browsers
(1)
Bugs
(2)
Business
(1)
C source code
(2)
Camera Hack
(1)
Chat
(1)
Chrome Os
(1)
computer_tricks
(122)
Computing
(4)
Corporate
(9)
Cracks
(5)
Crimes
(2)
Cyber Attacks
(12)
Cyber Crimes
(4)
Cyber Security
(51)
Cyber Threat
(19)
cyber_news
(30)
Database Hacking
(8)
Defaced
(2)
Dos
(1)
Dos Commands
(1)
Dos Tricks
(2)
Downloads
(7)
E_Books
(8)
Easy Applications
(6)
Email Security
(1)
Emails
(2)
Encryption Tools
(2)
Entrepreneur
(3)
Ethical Hacking Tools
(53)
Ethical Hacking Tutorial
(134)
Ethical Hacking Videos'
(12)
examples
(5)
Exploit
(19)
Facebook
(36)
Fakes
(1)
Featured
(19)
Footprinting
(3)
Gadgets
(20)
Gadgets_news
(14)
games
(3)
Gmail
(5)
Google
(32)
Google Dorks
(2)
Google+
(17)
Hacked
(3)
Hackers
(16)
Hacking
(74)
Hacking News
(4)
Hacking Softwares
(139)
Hacking Techniques
(112)
Hacking Tools
(144)
Hacking_news
(45)
Hacking_terms
(38)
Hackng with Mobile
(4)
Internet_Tricks
(3)
Java-Script Hacks
(1)
Keyloggers
(2)
Keys
(1)
Laptops
(1)
Latest Mobile Phones
(3)
Lecture
(1)
Linux
(6)
Loophole
(10)
Making Applications
(1)
Metasploit
(1)
Mobile
(11)
Mobile Applications
(3)
Mobile_tricks
(15)
Network Security
(6)
news
(50)
Nokia
(2)
Notepad Hacks
(1)
Operating Systems
(11)
Oracle
(1)
Password Cracking
(9)
Pendrive
(3)
penetration testing
(32)
phase_hacking
(9)
phishing
(6)
Photoshop
(11)
Programs
(1)
Protection Tools
(17)
Proxy
(2)
Scripting
(1)
Secure Computing
(38)
Security Bleach
(5)
Seminars_Work Shops_Demo
(5)
SEO
(15)
shell
(2)
shortcuts
(2)
Social Networking
(6)
Software
(70)
source
(4)
source code
(4)
SQL Injection
(9)
System security
(30)
Techie
(4)
Technology
(5)
The Pirate Bay
(1)
Torrent
(1)
Touch
(5)
Ubuntu
(3)
Updates
(2)
Video Tutorials
(4)
Virus
(20)
Vulnerability scanner
(9)
Vulnerable
(11)
Web Security
(13)
Web Traffic
(1)
Wifi Cracking
(2)
Windows
(7)
Windows Xp Tricks
(4)
Wireless hacking
(7)
workshop
(2)
Workshops and Seminars
(2)
worms
(1)
Xss Attack
(2)
Yahoo Messenger
(1)